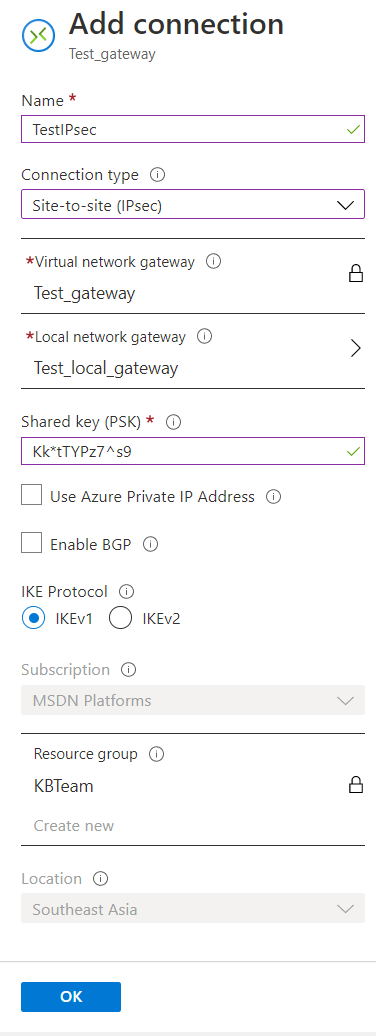
Sophos UTM: How to create an IPsec connection to Microsoft Azure Sophos UTM: How to tunnel between two UTMs which use the same LAN network range Sign up to the Sophos Support SMS Notification Service to get the latest product release information and critical issues. In Sophos Central, in the left-hand pane, select Settings. On the Settings page, under Administration, select Azure AD Sync Settings/Status. On the Azure Sync Settings/Status page, select Edit. In the Edit Azure AD Sync dialog box, enter the following information, which you obtained when you set up your Azure applications.
- See Full List On Community.sophos.com
- Azure Sophos Xg Firewall
- How To Use Azure MFA With Sophos UTM Firewall. - Rieskaniemi.com
- Sophos Utm Azure Sentinel
- Sophos Azure Configuration
- Sophos Cetral & Azure Sentinel Intergration – Sophos Ideas
Inspiration for this post was taken from: https://rieskaniemi.com/azuremfa-nps-extension-with-sophos-utm-firewall/
Some of the things that I’ve seen at work, is that Sophos UTM VPN users are using one token for Sophos SSLVPN and another for ex. Office 365 services. Both tokens can be in Microsoft Authenticator, but only the one that Office 365 is using, can do the “pop-up”, letting the user easy sign-in, like this:
Nonetheless it’s easier for the IT dept. (and the user!) to maintain only one token solution 🙂
Here is the auth flow for Azure MFA with NPS Extension:
Nice isn’t it 😉
So how to fix?
We setup Sophos UTM for RADIUS validation for SSLVPN and UserPortal access, and if you use the built-in OTP solution, disable that 🙂
To get started:

- If you do not have MFA enabled for your Office 365/Azure AD account’s you can enable it through following link: https://aka.ms/mfasetup
- And of course you need to have set Azure AD Connect to get your on-premise talking with Azure, I will not go into the details with this here, as I assume this is already setup and working 🙂
Let’s go:
- Install the Network Policy Server (NPS) role on your member server or domain controller. Refering to the Network Policy Server Best Practices, then you will find this “To optimize NPS authentication and authorization response times and minimize network traffic, install NPS on a domain controller.” So we will go ahead and place this on the domain controller, but remember it’s also possible to do it on a domain joined member server!
Press “Next” and the installation begins: - After installation has ended, go and join the NPS to the Active Directory, right-click NPS (Local):
- Download and install the NPS Extension for Azure MFA here:
https://www.microsoft.com/en-us/download/details.aspx?id=54688Note: As i did try this on a server with already setup NPS, it failed with the other mechanisms, because of this:
https://docs.microsoft.com/en-us/azure/active-directory/authentication/howto-mfa-nps-extension#control-radius-clients-that-require-mfa“
Control RADIUS clients that require MFA
Once you enable MFA for a RADIUS client using the NPS extension, all authentications for this client are required to perform MFA. If you want to enable MFA for some RADIUS clients but not others, you can configure two NPS servers and install the extension on only one of them.
Configure RADIUS clients that you want to require MFA to send requests to the NPS server configured with the extension, and other RADIUS clients to the NPS server not configured with the extension.”
So the “workround” is to run the MFA for the Sophos on a seprate NPS instance ?
- After it’s installed, go and follow the configure is like it’s stated here (Find TenantID and run Powershell script):
https://docs.microsoft.com/en-us/azure/active-directory/authentication/howto-mfa-nps-extension#azure-active-directory - Go and configure your radius Client, here it’s the UTM:
Remember the secret, we need it later on 🙂 - Create a “Connection request policy”:
See above the NAS Identifier, it’s “ssl”, it’s taken from this scheme:
Found here: https://community.sophos.com/kb/en-us/116144Just set like above, and the rest of the settings, just leave them to their defaults 🙂
- Now create a “Network Policy”
Add a domain group, that shall have this access, to simplify, here I have choose domainDomain Users
Now the EAP types, UTM does only support PAP, as far as I have tested:
You will get a warning telling you that you have choosen unencrypted auth (locally – not on the Internet!), just press OK.
Just left the rest to their default’s and save the policy. - Now to create a firewall rule:
- Now to setup the UTM for this:
Add new Authentication server:
Remember to choose RADIUS:
Fill in as your environment matches:Type in the secret you wrote down earlier and create a host object for your NPS, also remember to change the timeout from 3 to 15 secs!
You can now test is the authentication through NPS and Azure MFA is working, change NAS-Identifier to “ssl” type in a users username (e.mail adress) and password, and your phone should pop-up with Microsoft Authenticator 🙂
- Now to grant the RADIUS users access to SSL-VPN
Just add the built-in object “Radius Users” to your SSL-VPN profile:
- Now login to the User Portal and download a VPN client (You cannot use the old ones, if you already had thoose installed)
- Now connect through VPN, type in your full email in username and your password, then wait for MS Authenticator to pop-up, accept the token and you are logged into VPN 🙂
Sources:
Related Posts
Sophos made a great article regaring running Sophos XG with Azure AD authentication, here are the steps:
This document is applicable to all the XG Firewalls running all versions. To integrate the XG firewall with Azure AD, we need to create a new service called “Azure AD Domain services”.
With this integration, administrators can use Azure AD for the following:
See Full List On Community.sophos.com
- Captive portal authentication of internal firewall users.
- Authentication agent for windows, mac, linux.
- SSL VPN authentication.
- Sophos Connect client.
- Use the SSO using the Synchronized security UserID*.
Note: SSO with synchronized security and Azure AD needs to meet some specific requirements which are outside the scope of this document.
Azure AD DS replicates identity information from Azure AD to a Microsoft-operated set of domain controllers, so it works with Azure AD tenants that are cloud-only, or synchronized with an on-premises AD DS environment. The same set of Azure AD DS features exists for both environments.
Azure Sophos Xg Firewall
Azure AD domain services offer an LDAP interface to XG that can replicate the working of an on-premise Active Directory. This article assumes there is an existing Azure AD environment in place.

Table of Contents
- Login in to the Azure portal and create Azure AD domain services, this step will take 60-90 minutes to deploy. Please see the documentation from Microsoft on how to deploy Azure AD domain services.
- Once the AD domain services are deployed, you should see the health status as “Running”.
- Click on Synchronize, you can either select scoped or chose to synchronize all the Azure AD.
Note: The following step is required for cloud-only user accounts in Azure AD, as the Azure AD account is not synchronized with AD domain services until the user has changed the password by logging in to their office365 login. This password change process causes the password hashes for Kerberos and NTLM authentication to be generated and stored in Azure AD.
- Each user needs to login to the Office 365 portal and change the password. If it’s a new user logging into office 365 for the first time, they will be prompted for the password change.
- Once the AD domain services are deployed, it’s recommended to enable LDAPs if the firewall is sending LDAP bind request over the internet. For additional security, Sophos recommends creating an IPsec tunnel to Azure over which to bind the LDAP.
Note: Azure accepts self-signed certificates for this purpose. In this example, we use OpenSSL to generate a self-signed chain of certificates. Azure only accepts certs with “extendedkeyusage for server authentication”.
Below is the process to generate self-signed Certs with EKU:serverauth:
- In order to create the Certificate Authority Private Key and Certificate, you first need to create a private key for the CA with the name azureADca.key.
$ openssl genrsa -out azureADca.key 4096
Generating RSA private key, 4096 bit long modulus
……………………………………………………………………………………………………………………………………….++
…………….++
e is 65537 (0x10001) - Create the CA certificate to be used to validate signed certificates, called azureADca.pem.
$ openssl req -x509 -new -nodes -key azureADca.key -days 3650 -out azureADca.pem
You are about to be asked to enter information that will be incorporated
into your certificate request.
What you are about to enter is what is called a Distinguished Name or a DN.
There are quite a few fields but you can leave some blank
For some fields there will be a default value,
If you enter ‘.’, the field will be left blank.
—–
Country Name (2 letter code) []:CA
State or Province Name (full name) []:ON
Locality Name (eg, city) []:Burlington
Organization Name (eg, company) []:<Your org>
Organizational Unit Name (eg, section) []:Salesengineering
Common Name (eg, fully qualified host name) []:<Commaon name>
Email Address []:email@email.com - Create a text file and copy/paste the below text. Save the file as “azureAD-eku.conf” or any name of your choice.
[client_server_ssl]
extendedKeyUsage = serverAuth - Now that this file exists, you need to generate a private key for the LDAP cert with the name “ldapssl_private.key”.
$ openssl genrsa -out ldapssl_private.key 4096
Generating RSA private key, 4096 bit long modulus
……………………………..++
……….++
e is 65537 (0x10001) - Next, create a certificate signing request to sign with the CA you previously created with the name “azureADldapssl.csr” and fill in the following values in yellow.
$ openssl req -new -key ldapssl_private.key -out azureADldapssl.csr
You are about to be asked to enter information that will be incorporated
into your certificate request.
What you are about to enter is what is called a Distinguished Name or a DN.
There are quite a few fields but you can leave some blank
For some fields there will be a default value,
If you enter ‘.’, the field will be left blank.
—–
Country Name (2 letter code) []:CA
State or Province Name (full name) []:ON
Locality Name (eg, city) []:Burlington
Organization Name (eg, company) []:firewallinabox
Organizational Unit Name (eg, section) []:Sales Engineering
Common Name (eg, fully qualified host name) []:<yourdomainname>
Email Address []:<email@email.com>Please enter the following ‘extra’ attributes
to be sent with your certificate request
A challenge password []:<Password> - You now need to sign the request, while including the signing extensions created earlier. The following command will create the signed cert with the name “azureADcert.crt”.
$ openssl x509 -req -extensions client_server_ssl -extfile azureAD-eku.conf -in azureADldapssl.csr -CA azureADca.pem -CAkey azureADca.key -CAcreateserial -out azureADcert.crt -days 365
Signature ok
subject=/C=CA/ST=ON/L=Burlington/O=firewallinabox/OU=Sales Engineering/CN=firewallinabox.tk/emailAddress=email@email.com
Getting CA Private Key
$ - Convert the certificate into PFX format, as Azure accepts the certs in the PFX format.
$ openssl pkcs12 -export -out XGazureADcert.pfx -inkey ldapssl_private.key -in azureADcert.crt -certfile azureADca.crt
Enter Export Password:
Verifying – Enter Export Password: - Next, upload the XGazureADcert.pfx file into Azure AD.
- In order to create the Certificate Authority Private Key and Certificate, you first need to create a private key for the CA with the name azureADca.key.
- Under Azure AD domain service, navigate to properties and make a note of the following, Secure LDAP external IP address. If you are connecting through an IPsec tunnel, you can use the internal addresses which are 10.201.1.4 and 10.201.1.5 in this example.
- Make sure the admin group is selected with the correct administrator group used on the XG to send LDAP bind requests to AD domain services.
- In the Azure portal, navigate to Azure AD > Users and make sure the user is part of the AAD DC Administrators group inside Azure AD.
- In the Azure portal, navigate to the Network security groups > Inbound security rules, then add a new inbound security rule allowing the LDAPs traffic from your firewalls public IP. (This is optional and only required if you are using an IPsec tunnel for additional security).
- The administrator account you will be using on the XG Firewall must be first logged in to Office365, and the password needs to be changed upfront.
How To Use Azure MFA With Sophos UTM Firewall. - Rieskaniemi.com
- Login to the XG Firewall web UI and navigate to Configure > Authentication > Servers > Add and use the following settings we have from the Azure AD domain services.
- Import the groups from Azure AD as shown below.
- Select the server from the list of authenticated servers from Configure > Authentication > Services.
- Test the authentication with the user portal and the login should be successful.
Sophos Utm Azure Sentinel
Source: Sophos XG Firewall: Integrate XG Firewall with Azure AD – Recommended Reads – Sophos (XG) Firewall – Sophos Community
Sophos Azure Configuration

Sophos Cetral & Azure Sentinel Intergration – Sophos Ideas
Related Posts
